
How to Detect Network Intrusions ?
You could use Snort to detect emerging threats on your network. Snort is an open-source, free and lightweight network intrusion detection system (NIDS) software for Linux and Windows.
We will install first the software on a Linux VM and then create a rule to test the detection system.
sudo apt-get install snort
You can open the configuration file at /etc/snort/snort.conf
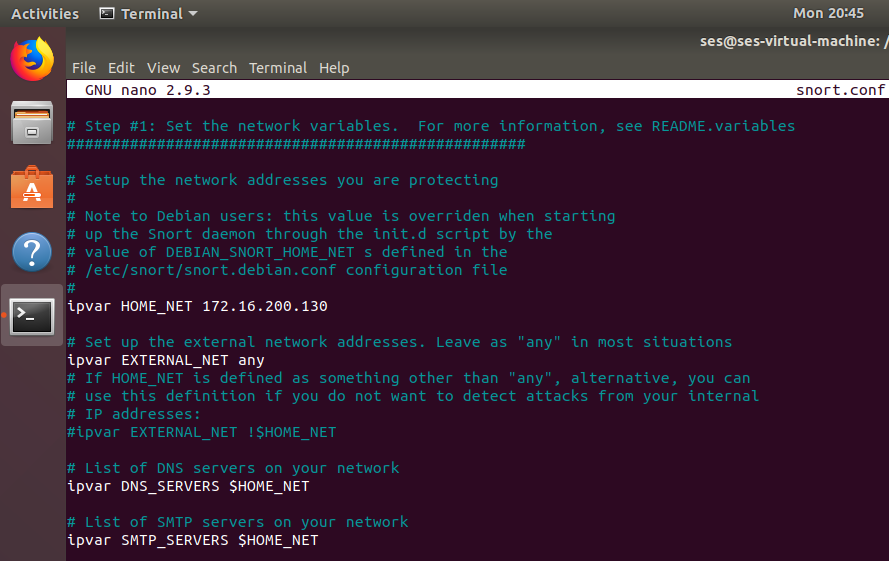
We need to define the “HOME_NET” variable, this setup the network addresses we are protecting.
In our Lab, we decide to protect the VM itself where Snort is installed.
You can then validate your configuration with this command :
sudo snort -T -i ens32 -c /etc/snort/snort.conf
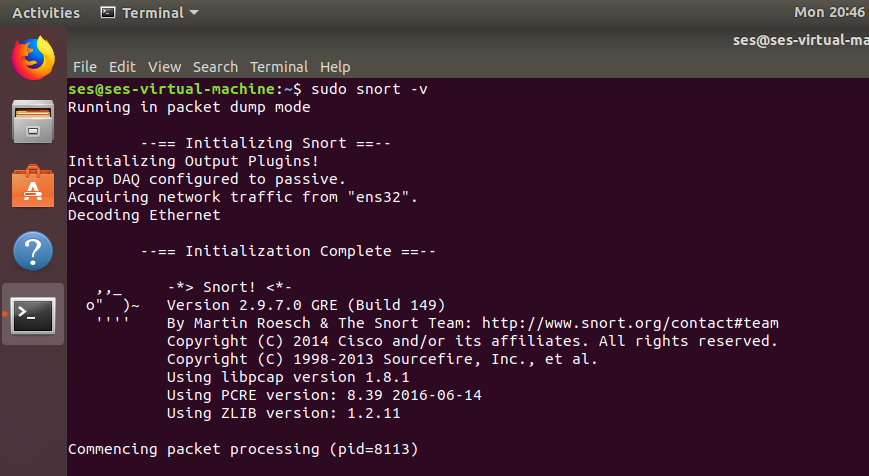
You can start Snort and check if the packets are processed :
Press CTRL + C to quit the dump mode.
Now, let’s create a rule to test the detection system, first go to /etc/snort/rules
To have automatic rules updates, register your Snort with PulledPork.
Then, edit the file local.rules and add an ICMP test rule :
alert icmp any any -> $HOME_NET any (msg:"ICMP test detected"; GID:1; sid:10000001; rev:001; classtype:icmp-event;)
By default, Snort is installed with root privileges, so it’s a good idea to create a snort user and group to run this network service :
sudo groupadd snort sudo useradd snort -r -s /sbin/nologin -c SNORT_IDS -g snort sudo chown -R snort:snort /etc/snort
Let’s start Snort in console mode to start the detections :
sudo snort -A console -q -u snort -g snort -c /etc/snort/snort.conf -i ens32
From a remote computer, let’s ping once the IDS :
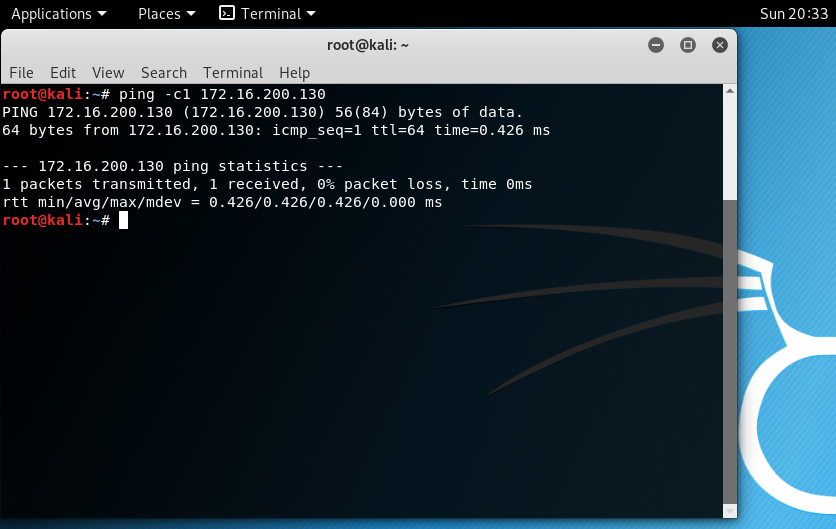
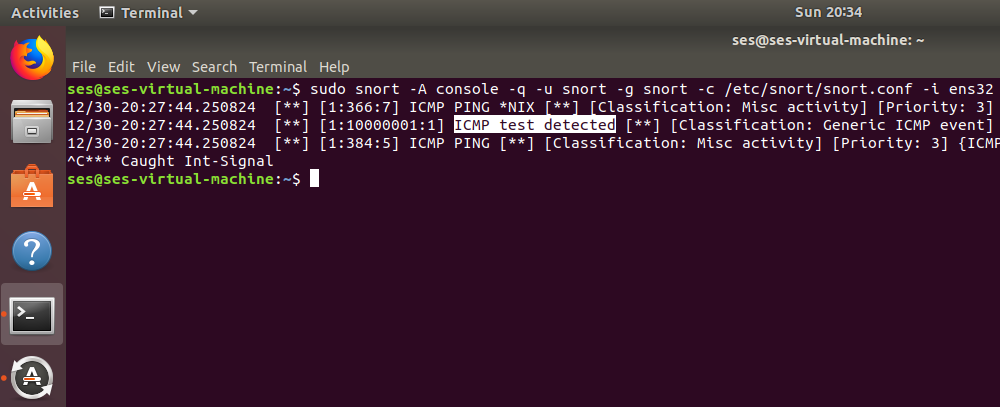
Snort detect the ping packets.
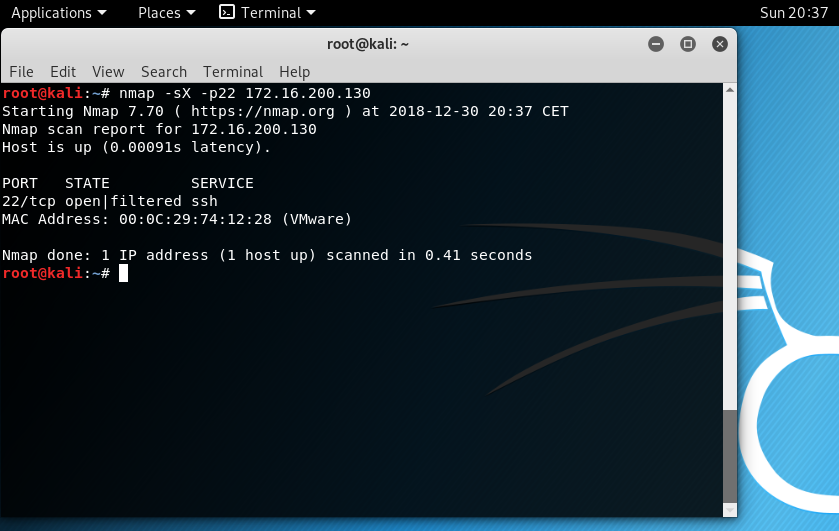
Snort detect the XMAS packets.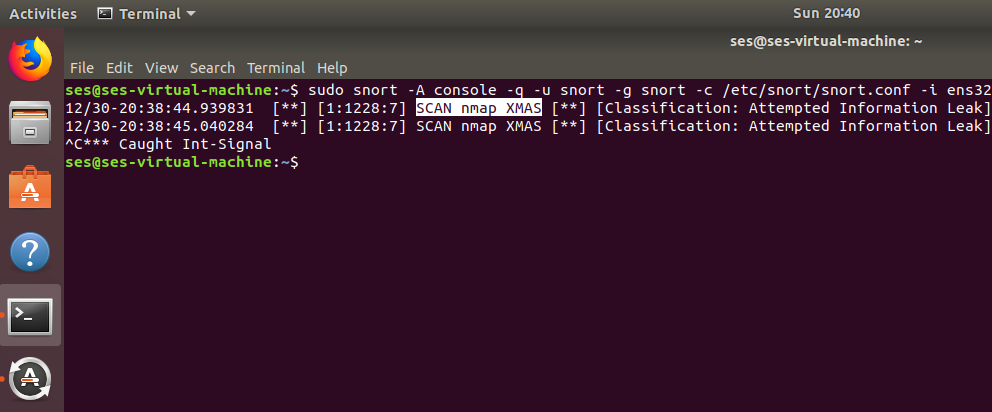
The IDS work as expected to detect emerging threats on your network. It could be configured as an Intrusion Prevention System and dynamically block computers, but keep in mind, that false positive could appear and reject legitimate machines.
Check the SNORT Users Manual : http://manual-snort-org.s3-website-us-east-1.amazonaws.com/snort_manual.html
And also the documents : https://www.snort.org/#documents
Leave a Reply